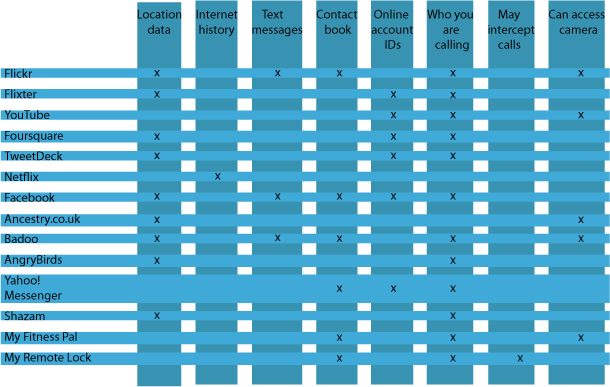
Listening to other persons calls is illegal, you can only monitor your own device if you don't want to be fined or to do some time in jail. However, in these days everybody listens to everybody.
How this works?
Some types of phone monitoring software are able to record phone
conversations and act as “bugs” that discretely tap into the phone’s
microphone so you can listen in on conversations.
The problem is that most of the time, there is no sure way to tell if someone is monitoring you or spying on your conversations.
Tips:
Listen for additional sounds on the line, such as popping, excessive static, humming or clicking.
The phone sometimes lights up when you are not using it.
Watch for interference with your radio and television.
The phone’s battery seems to drain quicker than usual.
The phone bill goes up and you are charged for more texts than you remember sending.
Check your phone for apps and downloads, but you might not find any software, even if you use "bugs" from surveillance companies this may not always work.
If you discover some software on your device or you are suspicious of some soft being installed, get rid of it by wiping the phones memory and go to your service provider, they can restore your phone.